Like many of our speakers this year, Alexandru Suditu loves a challenge. He’s had plenty of them as well while designing and implementing secure IT&C infrastructures from the ground up for companies in the energy sector. His focus expands beyond his role as Infrastructure & Security Manager at ENEVO Group, as Alexandru likes to explore the intricacies generated when security and operations meet.
We leaped at the opportunity to see things from his perspective, and we hope you’ll enjoy the interview that follows. With all the major attacks in past 6 months, we wanted to explore how the public perception changes as a result.
“For cybersecurity, there is surely no bad publicity as the more people are aware of the potential risks involved in using digital technology the safer we all are. As for the public perception, it’s hard to assess. I’m sure the general public now has a clearer view of the impact cybersecurity can have on their personal and financial lives, however, let’s keep in mind that we take our information from the news and not all articles are written by someone who has a professional understanding on cybersecurity.”
As infosec people know, there are many gaps we need to address. From a critical infrastructure point of view, Alexandru singled out an important one too look at:
“I would have to say the actual convergence of Operational Technologies with Information Technology. There is still a huge gap between the people who design/run these systems and people doing the cyber-protection.”
Securing critical infrastructure is a very appealing topic, especially when it comes to media headlines.
But what is the true risk of widespread cyber attacks on critical infrastructure? Are the doom and gloom scenarios close to reality or is it worse than we can imagine? Alexandru mentions that “it’s a very vast and complicated field that I think would be quite hard for any one individual to assess the chances of a catastrophic scenario”. “Most of the world uses pretty much the same technology and there aren’t a lot of well-known vendors for industrial control systems in the world, so you would have the same vulnerabilities across. On the other hand, most of these networks should be “air-gapped” or close to, so a widespread attack as vicious as WannaCry, for example, is not something we should be afraid of. However, as cybersecurity keeps evolving as a new dimension of war, we will always have those doom and gloom scenarios as we had with nuclear technology.”
Speaking of securing physical assets, we asked Alexandru how he believes organizations that manage critical infrastructure should balance physical security and cyber security.
“From my personal perspective, I feel that it was somehow easy for everyone to tighten up on the physical side of security, as they had something already going on, and are still looking at the cyber part and trying to figure out how to tackle it. The ones that were the most hit started moving on their own, developing internal competencies. Others are still waiting for some guidance/regulation from national authorities. Unfortunately, the latter has yet to decide how to tackle it itself. Cybersecurity for critical infrastructures, in general, I think is now where physical security for banks was 100 years ago. You have some thick walls and guards but lacking the high-tech surveillance systems.”
With everyone turning to the same, limited number of software products, how can these crucial organizations that control critical infrastructure avoid the risk of being exposed when a zero-day vulnerability emerges in any of them? “That is a good question. There was this one client that had his infrastructure developed in stages, and each stage was handed to a different vendor using different technologies. From an Operation and Maintenance point of view, it was a pain, but from the point of view of our discussion it does bring a positive side to it.”
We’re so used to everything being interconnected, but Alexandru firmly stands for keeping some things separate. “Critical Infrastructure should always be standalone as there is no need as in IoT for everything to be interconnected via the cloud. Critical infrastructures can’t be migrated to a modern infrastructure, as you would migrate an enterprise environment. As for control processes, you might find you need to change the entire process.”
For those of us outside this specialization, we thought of asking Alexandru how securing industrial control systems and other components of critical infrastructure compares to the security level of corporate networks and environments. “ICS don’t need to accommodate for the flexibility a human would require in performing his duties, therefore these systems can be more tightly locked down and usually are. It’s important to note that, for ICS, we are more interested in availability and integrity of the system, then confidentiality. This is a complete shift in the traditional CIA paradigm of corporate networks.”
Turning away from automation, the topic of the human element came to mind. The challenges in training and acquiring the right people are something he’s faced as well. “I think awareness is the most talked-about subject from this perspective. There are two sides of HR involved here: your entire staff that needs proper security training and awareness and your full-time cybersecurity personnel, for which there is scarcity in the labor market. For the latter, the skills required are an interesting and challenging mix: besides knowledge of general networking and basic enterprise deployment models, they also need to understand embedded devices and how they work, as most industrial devices are just that. And, most importantly, they need to have a general understanding of industrial control processes and how they work. It’s hard to understand the risks associated if you don’t understand what part each function of a device plays in the entire process and usually you really need the whole thing running.”
A core challenge for the tech industry and everything depending on it (which adds up to… everything) is balancing productivity and flexibility with security.
Alexandru’s take on it is to the point: “I feel the only way to balance innovation, flexibility, and productivity with security would be to make cybersecurity part of the working philosophy. Thankfully, for ICS there is a deep culture of security, both physical and process oriented which help build bridges and gather support for cyber security. For them, it’s like building a SCADA just for security.”
But a complex tech ecosystem relies on many elements to get the job down. One of them is complying with the law. While people usually tend to reject the idea of more regulation, Alexandru takes the opposite stance.
“Regarding ICS, I would like to see more regulation in Romania and Europe in general. We will have the NIS Directive come into play on May 18, 2018, which wants to ensure a high common level of network and information security across the EU. It requires member states to have identified the operators of essential services considered vital to the economy and society (energy, transport, water, financial institutions, healthcare, digital infrastructure, etc.), to take appropriate security measures to protect them and ensure they comply with national laws regarding cybersecurity. Companies tend to look at what regulations requires them to have in place as a sort of baseline, so, in general, it helps to have that.”
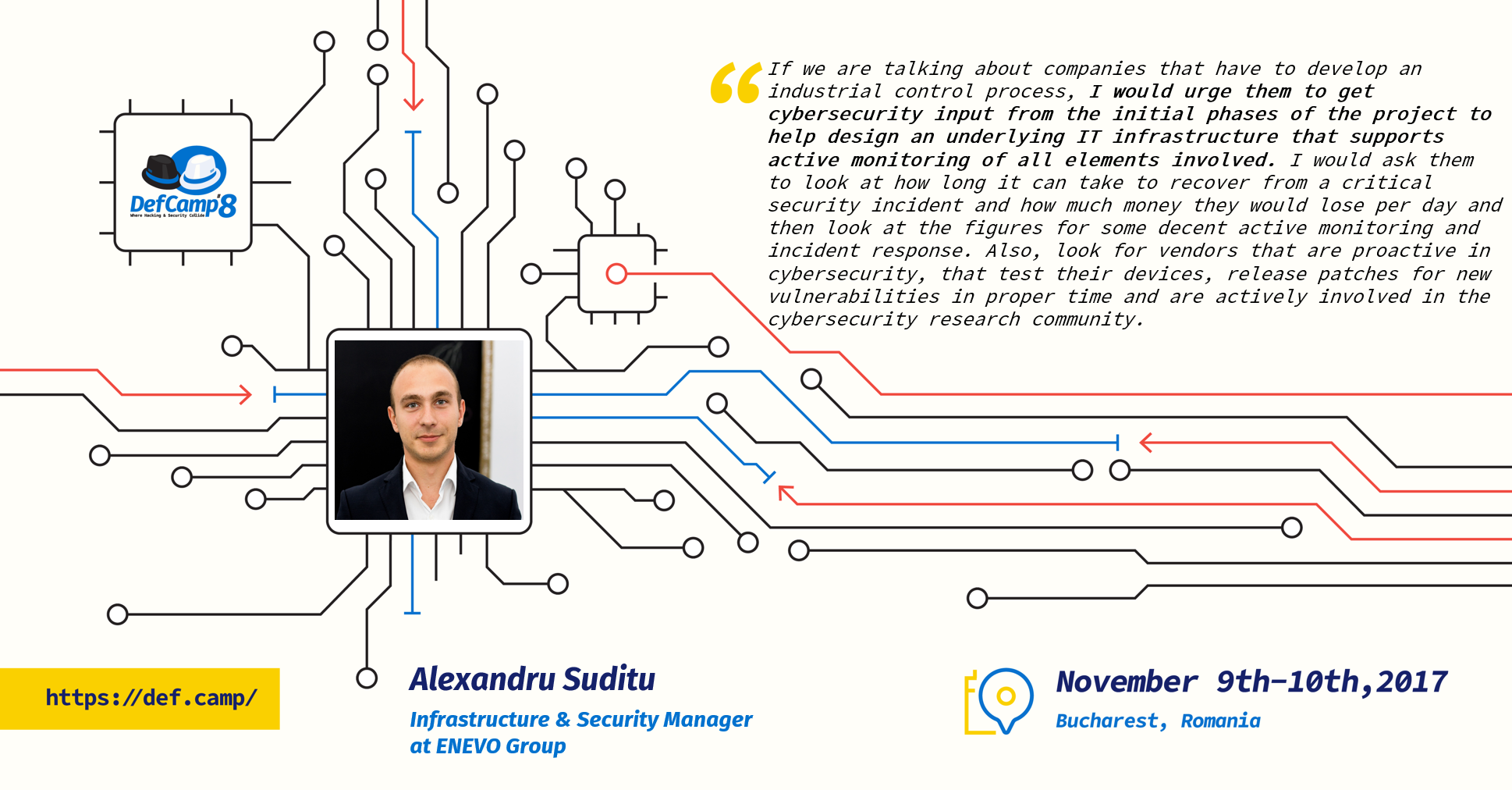
But what if you’re just getting started? When it comes to companies who are just beginning to focus on building their security infrastructure (prompted by the EU GDPR or not), Alexandru suggests some critical elements they shouldn’t overlook. “If we are talking about companies that have to develop an industrial control process, I would urge them to get cybersecurity input from the initial phases of the project to help design an underlying IT infrastructure that supports active monitoring of all elements involved. I would ask them to look at how long it can take to recover from a critical security incident and how much money they would lose per day and then look at the figures for some decent active monitoring and incident response. Also, look for vendors that are proactive in cybersecurity, that test their devices, release patches for new vulnerabilities in proper time and are actively involved in the cybersecurity research community.”
From a local perspective, we asked Alex to evaluate the state of Romania’s critical infrastructure in terms of security. He suggests an approach that anyone could use to shape his/her own opinion:
“I’m not sure if it would be appropriate for me to perform such an assessment as most documents portraying to critical infrastructure are classified and require ORNIS clearance. However, if we were to dig through publicly available information, we should look for signs of cyber maturity like designated personnel for ICS Cybersecurity in the company organization chart, or a number of disclosed security breaches. We could go to LinkedIn or any jobs site or even the careers section of some of the companies that own and operate infrastructures that under the current national legislation might be considered critical. We know this is a new field and it’s not a competency easy to develop in-house. But when everyone is silent, and no one is hiring, I feel that speaks for itself about where we are in our endeavor to secure our critical infrastructures.”
With that in mind, we’re sure that Alexandru’s presentation about the Evolution of threats to Electric Power Grid Operations will bring out many more questions than we included in this interview. See you soon (so, so soon!) at Defcamp 2017!
The interview & editing was made by Andra Zaharia.
DefCamp 2017 is powered by Orange România and it’s organized by the Cyber Security Research Center from Romania (CCSIR) with the support of Ixia, a Keysight Business as a Platinum Partner, and with the help of Bitdefender, SecureWorks, Amazon, Enevo Group and Bit Sentinel.