Learning from our speakers is one of the things we love most about DefCamp. Providing the right context for knowledge-sharing was one of the initial goals when we started this community-driven event and we’re happy that it still fuels us today.
So today we’d like to share some wisdom from April C. Wright, one of the DefCamp speakers whose talk is among the most anticipated. April is a Senior Security and Compliance Manager for Verizon Wireline, where she deals with the complexity of massive tech infrastructure and the people behind them. Her objective is to secure, educate and leave behind lasting security programs that make a real difference.
We first wanted to explore the topic of internal and external challenges that organizations face nowadays in terms of securing their assets and keeping them safe. April pointed out a few of the most important ones:
“One of the biggest challenges I am concerned with is that we are spending time, money, and effort to protect assets that are not completely understood. The same amount of resources are being put into securing the externally facing web server as are being put into securing a back-office reporting tool. This happens because it’s easier to apply the same protections to everything across the board than to actually suss out what data is being protected and why. So, data ends up either over-protected or under-protected. Application whitelisting, for example, is a huge pain to setup, so it’s ok to only use it on the most critical infrastructure (if not doing it everywhere is acceptable to the company’s risk profile).
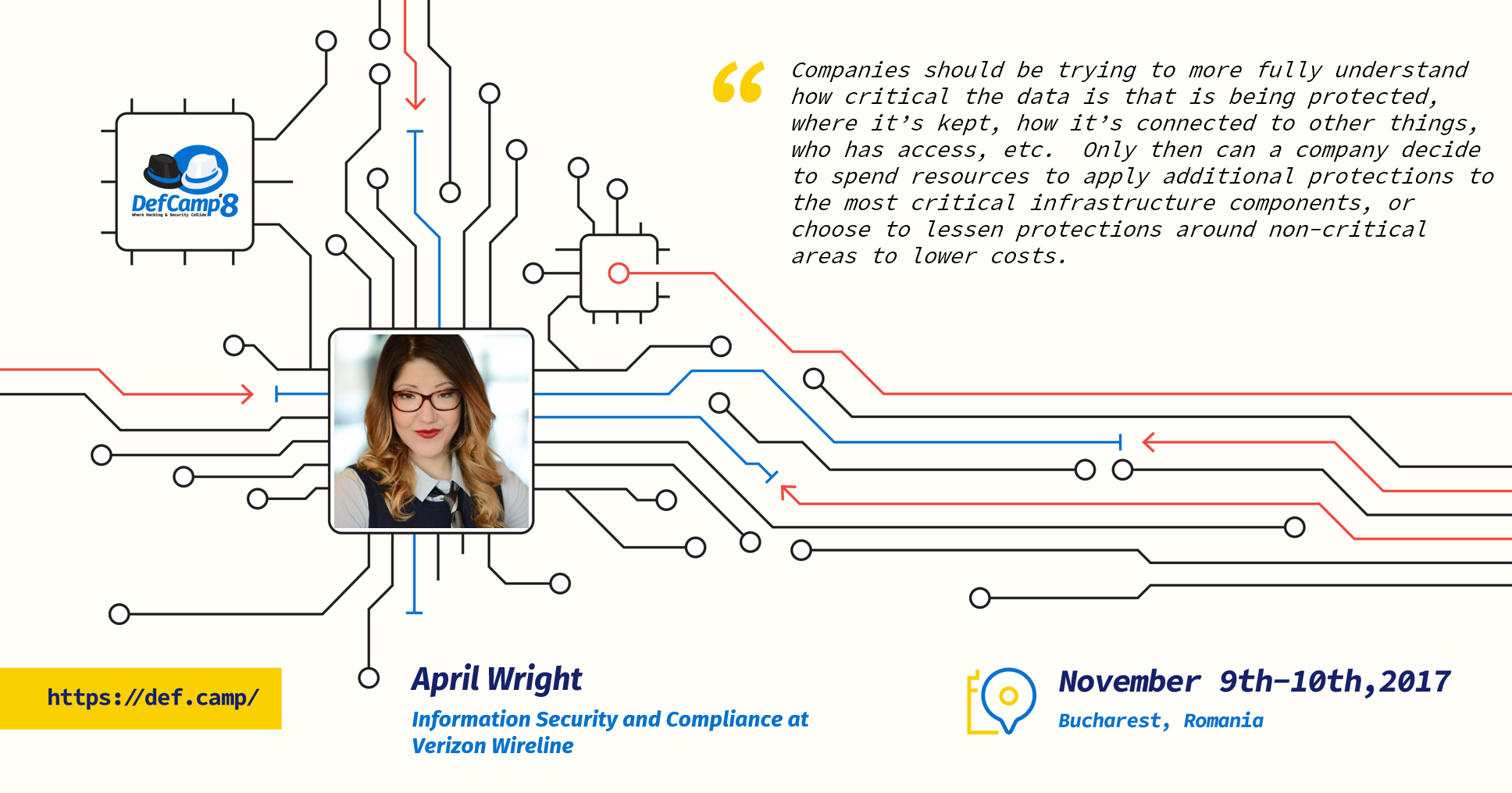
Companies should be trying to more fully understand how critical the data is that is being protected, where it’s kept, how it’s connected to other things, who has access, etc. Only then can a company decide to spend resources to apply additional protections to the most critical infrastructure components, or choose to lessen protections around non-critical areas to lower costs. Defenses and detection should be commensurate with the data’s importance, with the environment, and with the risks faced by the data.”
The challenges that April mentions and what cascades from them require a different approach, a change in mindset. But what values and psychological triggers should cyber security specialists appeal to in order to help integrate cyber security as part of the mindset in a company or, on a larger scale, of most people who use the Internet and technology in general?
April put the dot to the i when replying that “An organizational culture of security starts with the Leadership team (i.e. from the top).” She also emphasized that “When a company appreciates the importance of security or privacy, it shows in everything they do, and their decisions will be guided by those values. A company (or society) may need to stand up for what is right in the face of demands being made that may violate their ideals of security/privacy. Doing what is “right” is important when protecting the privacy of employees, users, or citizens.”
What’s more, her experience proved that “Positive reinforcement of good behavior is always better than negative. Gamification and rewards can trigger competitiveness to achieve, and when used in an infosec context, employees can become encouraged to exhibit more security awareness. For example, punishing an employee for failing to report a phishing email is NOT going to be as effective as offering a prize to the employee with the most phishing emails reported at the end of the fiscal quarter.” But do people really change their minds? It’s easier to see these shifts through the eyes of a specialist who’s been in the field for over 25 years.
“Security is finally at the forefront of people’s minds, but it’s not always in a good way. People understand that there are malicious entities out there, and most people have probably had their identity involved in a breach at some point. The average person still does not necessarily understand what their individual role is in the larger picture, or what it takes for us to defend against the bad actors. Our work is challenging and sometimes thankless.
Infosec is like fighting an uphill battle, and it definitely takes a village. There is a much larger community of hackers and infosec defenders today, which is a very good thing. We are learning and sharing and growing together. Unfortunately, today the average person is far more likely to hand over their personal info for a $5 online gift card than they were. Whether it’s targeted advertising, social media, or creating an account during shopping cart checkout, we are mindlessly handing over our data every day to we-don’t-even-know-who for we-don’t-even-know-what. P.S. if a service costs you nothing, you are the product!
I see people caring less about privacy as a basic human right and more about things they want being easy or cheap. How many contests and sweepstakes exist solely to gather user data? If we had to pay out of pocket for social media, it definitely would not exist like it does today. There are good things, too, as so many of us are trying to fight the good fight. Take for example the free service LetsEncrypt, which is getting more people using TLS certificates. Or security tools like no-cost anti-malware or encrypted password managers. When security and privacy become more simple and inexpensive, it’s going to make a huge difference to society.”
But if learning does happen, what’s the speed of private organizations, government institutions and private users? This brought on some issues deeply embedded into our tech ecosystems. “Even “security companies” are releasing insecure software. We have a long way to go in that area. Companies are getting better in terms of finding and fixing vulnerabilities, and programs like bug bounties are helping with those efforts. However, we are not getting much better about *avoiding* the bugs in the first place. Software development is still in the “dark ages” when it comes to secure design, architecture, and coding. All companies want to get software out the door as quickly as possible to make revenue and hit numbers, but this ethos is doing more harm than good. The status quo of “If you are not embarrassed by the first version of your product, you’ve launched too late” (quote by Reid Hoffman, the founder of LinkedIn) is leading to the creation of software that is insecure from the start, which puts all of our data at risk.
Businesses are willing to accept the risk of your data being exposed in order to get new features out the door before their competitor. This is a mindset that needs to change. Software is only as secure as the foundation it’s built upon.
Sometimes, though, in spite of best efforts, cyber attacks do happen. Let’s take data breaches, for example. How would a company survive such an event?
“Good PR? 🙂
Consumers seem very willing to overlook the cause and effect of data breaches, and it is almost expected by both companies and the public. As defenders, we should be more focused on preventing breaches than we are.
Fines are not doing anything to prevent malicious hacks, and disclosure-related expenses are becoming just part of the cost of doing business. Once your data is out there, it’s out there forever. We need a vaccine, not an ambulance.”
However, the path to developing a vaccine is paved with buzzwords, such as “machine learning”, “second generation antivirus” and others. April helped pull the curtain and catch a glimpse of what’s behind them.
“Everything today is pretty much the next generation of something that came before it. It’s important that we get past the hype of product marketing and evaluate not only what a product really does, but also what it does not do well. Machine learning has a lot of potential, but like anything, it totally depends on how it’s used.
Just because it’s a machine does not mean it is infallible. Machines are only as good as the humans who create them. Any technology needs to be part of a larger ecosystem that includes human awareness, appropriate detection, and built-in defenses.
There is no such thing as completely “secure”, there is only “decreased risk”. If a second generation antivirus truly decreases your risk, that’s great. However, if it is just as good as the first generation, then it’s just hype.”
We wanted to take advantage of this opportunity to pick April’s brain about a “hot” issues: the biggest fears that companies have related to sharing intelligence.
“There is some merit to a fear of sharing unfiltered intelligence because it could contain secrets or proprietary information. However, aggregated data, like the Verizon DBIR (Data Breach Investigations Report) can be of great help to organizations who want to learn from things they have not directly experienced. Companies may be afraid of losing competitive advantage if their breach data and intelligence are somehow used against them, i.e. to harm their brand.
Many services are going about collecting this information with the sole intent of sharing it, either as real-time threat maps or historical data, and actually making money off of it because it is valuable data! Smart companies are both contributing to and consuming this information to their advantage; if an organization doesn’t understand the current threat landscape, how can it protect itself?”
If everything falls into place at the end of the day, do companies have a talent pool to choose from? In her fast-paced career, April has definitely experienced challenges when recruiting, we thought. Not only did she confirm it, but she also had some solutions lined up!
“Yes, a thousand times yes, there is a shortage of infosec talent.
Really good infosec people are as difficult to find and retain as unicorns.
One way to deal with this is to build security teams at scale. In other words, hire a few people to fulfill a job role rather than one person. Let’s say you want to find a programmer with red team experience that can also manage a team of people. Instead of hiring one person, hire three people – a developer, a red teamer, and a manager – and have them work together.
In addition to opening up the choice of available candidates, this approach helps in a few ways: First, you end up with less of a single point of failure. If you have one security person and they go on vacation, there is a problem. If you have 3 or 4 on a team and one person is out, it’s not as much of a big deal. Second, you end up with more people learning infosec and growing as contributors, which actually adds to the talent pool over time. Third, it’s diverse teams solve problems faster than non-diverse teams or individuals, so by having people from different backgrounds working together, you will get more of a balanced approach to problem=solving and thus end up with a more holistic security posture. By having people with different skill sets working together, they learn other points of view and develop ways to think with new perspectives.”
Needless to say that April’s words of wisdom will most likely continue to be relevant and useful for years to come, even as the infosec landscape changes.
This was just a taste of the many things we’ll learn in less than two months, when April will be on stage to talk about one of her favorite topics. Her presentation will tackle one of the key issues mentioned before: “Orange is the New Purple – How and Why to Integrate Development Teams with Red/Blue Teams to Build More Secure Software”.
Get your front-row ticket for her talk and many others which will put core infosec issues into the spotlight!
The interview & editing was made by Andra Zaharia.