Please note that this page represents an archive of Innovative Products & Technologies showcased at DefCamp’s 2016 edition. If you are looking for similar opportunities this year, please check the latest edition of Technologies.
Summary of what you can find
- Business Internet Security Threat Map, Mobile Wi-Fi, Wi-Fi in Transit from Orange Romania
- AVDS & beSTORM from Beyond Security
- Bitdefender
- ThreatARMOR™ from Ixia
- Threat Intelligence Services from SecureWorks
- CyberGhost Premium Plus
- SOC, SIEM and Industrial/SCADA solutions from PwC
Business Internet Security Threat Map
Business Internet Security from Orange protects the information delivered over the internet and the companies’ data against cyber-attacks. The data traffic is scanned for viruses, malware, spam, intrusion attempts and it is cleaned in the cloud, before is reaches the companies’ servers. With a simple management interface, permanent updates and upgrades, embedded professional services and security consultancy and seamless scalability and upgradability, Business Internet Security eliminates the need for expensive, on-premise equipment.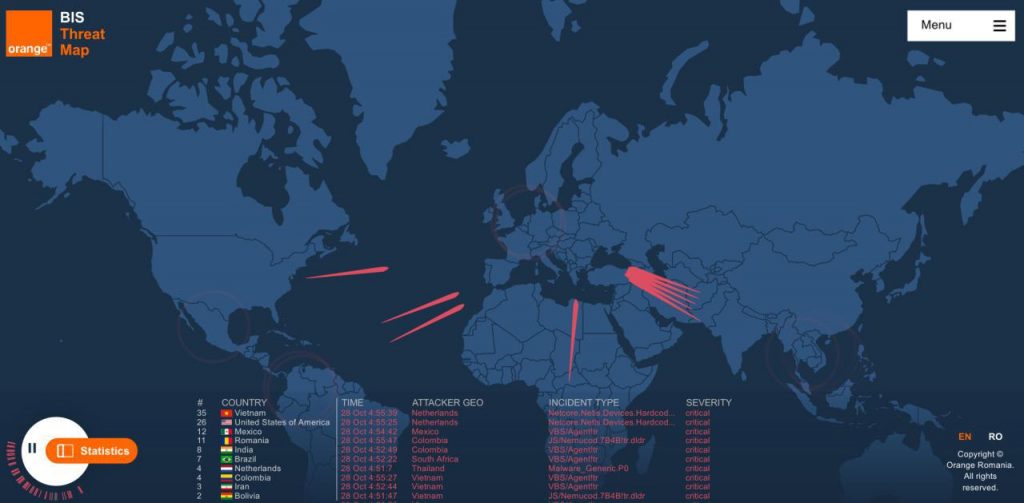 As an add-on to the service, the BIS Threat Map provides real time visualisations of cyber-risks and attacks from and to Romania, with relevant statistics by industrial verticals. This way, companies present in Romania can understand what is the threat level and types of risks they might face and take proactive measures. For detail, visit https://bis-threatmap.orange.ro
As an add-on to the service, the BIS Threat Map provides real time visualisations of cyber-risks and attacks from and to Romania, with relevant statistics by industrial verticals. This way, companies present in Romania can understand what is the threat level and types of risks they might face and take proactive measures. For detail, visit https://bis-threatmap.orange.ro
Orange Mobile Wi-Fi
Mobile Wi-Fi is a technology that is exlusively deployed by Orange in Romania and allows for a seamless integration of the mobile network and Wi-Fi. Orange customers are able to connect to Orange hotspots automatically with end-to-end encryption, without the need to manually select a network or input any password, using credentials stored on SIM cards. The technology is embedded in both Apple and Android operating systems.Wi-fi in Transit
 Wi-FI in Transit is the only Wi-Fi service in Romania specifically developed for public transportation. It is already helping local authorities deliver high speed mobile connectivity to citizens in Cluj, Alba Iulia, Timisoara, Caransebes, and enables always-on connectivity for international bus travellers. Business Wi-Fi Mobile is also installed in several trains operated by CFR.
Wi-FI in Transit is the only Wi-Fi service in Romania specifically developed for public transportation. It is already helping local authorities deliver high speed mobile connectivity to citizens in Cluj, Alba Iulia, Timisoara, Caransebes, and enables always-on connectivity for international bus travellers. Business Wi-Fi Mobile is also installed in several trains operated by CFR.
Bitdefender
 Bitdefender is a global security technology company that provides cutting edge end-to-end cyber security solutions and advanced threat protection to more than 500 million users in more than 150 countries. Since 2001, Bitdefender has consistently produced award-winning business and consumer security technology, and is a provider of choice in both hybrid infrastructure security and endpoint protection. Through R&D, alliances and partnerships, Bitdefender is trusted to be ahead and deliver robust security you can rely on.
The company’s most recent innovations – Bitdefender BOX, the breakthrough solution that protects all a user’s connected devices, and Hypervisor Introspection (HVI), a revolutionary framework to secure virtualized environments from advanced targeted cyber-attacks – supported Bitdefender’s thought leadership positioning and named it a Visionary company in Gartner’s Magic Quadrant for Endpoint Protection Platforms.
Bitdefender is a global security technology company that provides cutting edge end-to-end cyber security solutions and advanced threat protection to more than 500 million users in more than 150 countries. Since 2001, Bitdefender has consistently produced award-winning business and consumer security technology, and is a provider of choice in both hybrid infrastructure security and endpoint protection. Through R&D, alliances and partnerships, Bitdefender is trusted to be ahead and deliver robust security you can rely on.
The company’s most recent innovations – Bitdefender BOX, the breakthrough solution that protects all a user’s connected devices, and Hypervisor Introspection (HVI), a revolutionary framework to secure virtualized environments from advanced targeted cyber-attacks – supported Bitdefender’s thought leadership positioning and named it a Visionary company in Gartner’s Magic Quadrant for Endpoint Protection Platforms.
AVDS & beSTORM from Beyond Security
Beyond Security’s security testing solutions accurately assess and help resolve security weaknesses in networks, web applications, critical industrial systems and networked software. We help businesses and governments simplify and improve the accuracy of their security testing and thus reduce their vulnerability to attack and data loss. Our product lines, AVDS (network and web application vulnerability assessment) and beSTORM (software security testing), will help you secure your network and applications, comply with your own security policy requirements and exceed industry and government security standards. The AVDS family of network vulnerability assessment and web application security testing solutions are the most accurate and easiest to use in the industry. The AVDS product line has a VA solution for businesses and government units of any size. It will find, prioritize and manage the repair of security weaknesses in your network and in web applications with the fastest setup and the least maintenance.- Behavior based scanning with near zero false positive rate
- Non-intrusive: safely scan production equipment and apps during work hours
- Integrated network, web application and database testing
- Automatically finds new active IPs, applications, Wireless Access Points
- Fast and easy to deploy, requires no installation of ‘agents’
- Concise, actionable reporting with range of report types
- PCI approved scanning of external IPs included
- Scalable, 50 to 500,000 IPs
- Secure and cloudless: Sends no data out of network
- Development language independent
- Integrated tests with CVE information
- Easily generate binary data of tests
- Easily adapted to new testing environments
- Hands free testing – automatic stop and restart
- Custom Protocol support
- IPv6, IPv4
- Auto-learn new protocols
ThreatARMOR™ from Ixia
ThreatARMOR™ establishes a new front line of defense in clients’ networks, removing threats and improving security ROI by eliminating unwanted traffic before it hits any existing security infrastructure. It prevents network probes, phishing clicks, and all traffic to and from untrusted countries. This reduces the risk from attacks such as zero-day ransomware mutations along with up to 80% of the malicious connections that threaten the network and generate floods of security alerts. A single ThreatARMOR security appliance can be deployed on both the inside and outside of a company’s perimeter, identifying infected internal systems and blocking communication with Botnet controllers while reducing inbound firewall load from known bad sites and countries clients don’t do business with. Even encrypted connections from those sites are automatically banned. ThreatARMOR complements next-gen firewalls by offloading massive-scale blocking so that they can allocate more resources to content inspection, user policies, VPN termination, and other features while generating fewer security alerts.Threat Intelligence Services from SecureWorks
 Cyber threat intelligence is evidence-based information that identifies emerging threats to your organization and helps mitigate your exposure to them. An efficient threat intelligence security team analyzes and prioritizes global and targeted threats, so your organization can proactively prevent security attacks. Take advantage of our threat intelligence gleaned through scale and visibility across 4,200+ client environments around the world. Developed by the SecureWorks Counter Threat Unit™ (CTU) research team, we develop cyber threat intelligence your organization can readily take action on.
Cyber threat intelligence is evidence-based information that identifies emerging threats to your organization and helps mitigate your exposure to them. An efficient threat intelligence security team analyzes and prioritizes global and targeted threats, so your organization can proactively prevent security attacks. Take advantage of our threat intelligence gleaned through scale and visibility across 4,200+ client environments around the world. Developed by the SecureWorks Counter Threat Unit™ (CTU) research team, we develop cyber threat intelligence your organization can readily take action on.
CyberGhost Premium Plus
 CyberGhost Premium Plus offers access to more than 700 servers in 30 countries around the world. CyberGhost Premium Plus is suitable for up to 5 devices and integrates the following profiles to guarantee a seamless, unique online experience:
Surf Anonymously, Unblock Streaming Websites, Protect Wi-Fi connection, Torrent Anonymously, Unblock Basic Websites, Choose My VPN server.
The following features are included:
CyberGhost Premium Plus offers access to more than 700 servers in 30 countries around the world. CyberGhost Premium Plus is suitable for up to 5 devices and integrates the following profiles to guarantee a seamless, unique online experience:
Surf Anonymously, Unblock Streaming Websites, Protect Wi-Fi connection, Torrent Anonymously, Unblock Basic Websites, Choose My VPN server.
The following features are included:
- Guaranteed IP Change
- No Logs
- Unlimited Bandwidth and Traffic
- AES 256-BIT Encryption
- Anonymous Surfing
- Unblock Basic Websites & Streaming Services
Security Operations Centers (SOC) and Security Information and Event Management (SIEM) solutions
We can help you detect and react faster to security incidents by designing and building turn-key Security Operations Centers (SOC):
- Designing security monitoring and incident handling processes,
- Implementation of security reporting system, and SOC supporting tools and infrastructure.
- Improving maturity of existing processes and SOC technologies
- Providing turn-key implementation of SIEM technology, including design, installation, configuration, data sources integration and use cases
- Analysis of currently used monitoring tools and SIEM
- Analysis of existing IT Security Architecture
- Analysis of various business and regulatory drivers affecting security monitoring
- Proposal of requirements for SIEM and SOC solution
Industrial / Operational Technology / SCADA Security
We have developed an OT Security Architecture, which includes the whole spectrum of OT Security Assessment Services:- OT Security Risk Assessment
- OT Networks Design
- Process Impact Analysis
- OT-related Fraud Investigation
- OT Security Solution Design
- OT Security Solution Implementation
- OT Security Procedures and Standards
- OT Security Trainings
Sponsors & Partners
They help us make this conference possible.
POWERED BY
Orange Romania is part of the Orange Group, one of the largest global telecommunications operators that connects hundreds of millions of customers worldwide. With over 11 million local customers and an annual turnover exceeding 1.5 billion euros, Orange Romania connects 1 in 2 Romanians and offers an extensive range of communication solutions for both individual and corporate customers, from basic connectivity services to complete mobile, fixed internet, TV packages, and complex IT&C solutions through Orange Business.
Orange Romania is the number 1 operator in terms of network performance, and also holds nine consecutive Top Employer certifications, which confirm that Orange Romania, in addition to the remarkable products and services it offers, pays special attention to its employees and working environment. In the past 3 years Orange has launched two 5G Labs in Bucharest and Iasi, that aim to support researchers, startups and companies to test their 5G solutions in advance.
In addition, Orange is a long-term supporter of the startup ecosystem through the Orange Fab accelerator program designed to support entrepreneurs in the development of innovative products and their distribution locally and internationally.

































