Inbar’s experience spans since before the infancy of the Internet to today’s challenges in terms of security and beyond. He’s been doing reverse engineering since he was 14 and spent most of his career in info security.
Inbar’ skills could’ve landed him behind bars a long time ago, but he chose to be a defender at an early age. His work with finding and explaining vulnerabilities has been the topic of many talks at security events around the world.
This year, Inbar is coming to DefCamp again to share his experience and wisdom.
First, we wanted to get Inbar’s opinion on how the usual home user feels about all the headlines regarding data-breach and other cyber threats. What set the expectation of 100% security and how is this changing?
“No, it was never 100% secure. In fact, in the early days, it was even less secure because there was no security at all. What we have now is not insecurity but rather faulty security. Also, I don’t think there was ever an expectation of 100% safety or even a sense of it. I think there were fewer breaches that were both detected and published. Now that it’s all public, we get the feeling it’s all over. In the current state of things, I don’t think it’s getting any better because the core problem is that vendors keep releasing vulnerable products. As long as that doesn’t change, nothing else will.”
So acknowledging that no system is 100% secure – how can customers and users deal with that? How can we engage them to share the responsibility of their own data’s safety on and offline?
Inbar believes that “there are common practices that users need to adopt.
The most important two are:
1) Data Backup – If something is very important to you, have another copy of it somewhere. Preferably offline (unlike an external hard drive that’s always connected).
2) Unique Passwords – Your passwords must not be used in more than one place. You can argue and complain, but this is an undeniable truth. Leaked passwords are fed to automatic scanners that try them at major services. Make even a small change, but make it.”
But the rise in popularity and exposure for cyber can bring on security fatigue. How do we avoid FUD but still be persuasive?
“FUD is a sales promoter, not an educational tool, so I don’t see it decreasing anytime soon. If you want to change people’s habits you need to explain the risk and give them directions and tools for dealing with it. Just scaring them causes antagonism and scepticism.”
We also picked Inbar’s brain about the distortions in the way infosec is presented by the media.
“The fact that all hackers are portrayed as bad, and that legitimate vulnerability research is presented as criminal and bad. The ethical vulnerability researchers are working to make the world a better place by forcing the vendors to fix their products and exposing their negligence at times.
Responsible and coordinated vulnerability disclosures, as well as bounty programs, should be encouraged.”
From the outside, it may seem as the defenders are much too late behind on the attackers. We wanted to find out how it looks like from the inside and how defenders can communicate the wins so users have a more balanced outlook.
“Most of the time this is the reality. The attackers have the initiative and the defenders respond.
Every now and then there is a new defensive technology that is a game-changer, but most of the time it’s just another solution to another problem.
If the effort was directed at increasing the quality of software instead of chasing ways to abuse it, then a change would happen.”
When it comes to critical infrastructure, what can regular users do to push companies whose products and services they buy to strengthen their cyber security, thus extending this protection to them?
“Leave the vendor. That’s the only incentive. Consumers should require the vendor to present what they’ve done in terms of securing the product, and make it clear to the vendor that they will be punished if their products prove to be easily hacked. It’s easier said than done, of course, but perhaps starting to sue vendors who prove to be reckless will also make a difference.”
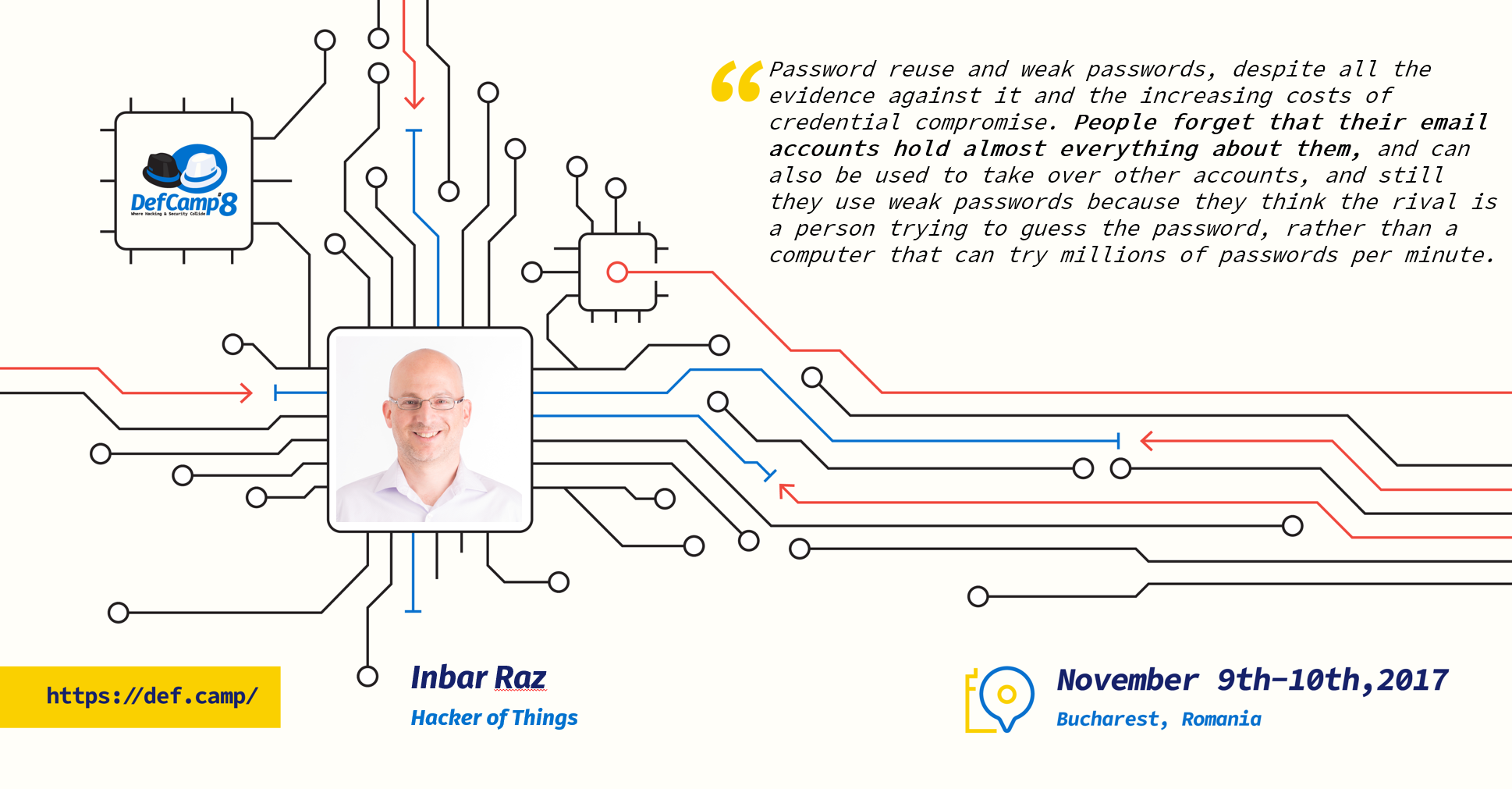
The next thing we asked Inbar was: What is one pervasive attitude about cyber security observed in home users or companies that intrigues you and why?
“Password reuse and weak passwords, despite all the evidence against it and the increasing costs of credential compromise. People forget that their email accounts hold almost everything about them, and can also be used to take over other accounts, and still they use weak passwords because they think the rival is a person trying to guess the password, rather than a computer that can try millions of passwords per minute.”
Looking forward to the future, will securing one’s devices and data ever become less of a hassle for individual users and even companies?
“It’s hard to tell. As I said before, as long as all new products keep coming up with security vulnerabilities in them, we are going to stay at the exact same place.”
So what can each of us do to contribute to safer habits online and offline? Here’s what Inbar said he found effective in his experience:
“Stop trusting emails with links, and carefully examine the content of any email that asks you to click a link. Is the language correct? Have you ever received a similar email that was legitimate? Did it look the same?”
We’re really excited to have Inbar join us on stage this year at DefCamp and he confessed he’s looking forward to meeting “the great community that he discovered last year”.
DefCamp 2017 is powered by Orange România and it’s organized by the Cyber Security Research Center from Romania (CCSIR) with the support of Ixia, a Keysight Business as Platinum Partner, and with the help of Bitdefender, SecureWorks, Amazon, Enevo Group and Bit Sentinel.
The interview & editing was made by Andra Zaharia.