It had to happen onsite this year
Our 2022 kicked off with a strong feeling of nostalgia, after a fully online DefCamp 2021 just a few months earlier, and with a very intense virtual edition of D-CTF 21-22.
These had us longing for what we knew HAD to happen:
DefCamp.
The 2022 edition.
Together, with all of you.
Under the same roof.
Onsite, in Bucharest.
And it finally did – and the energy was amazing!
One month after DefCamp and we’re still fueled by the experience – we hope you are too. Over 40 national and international speakers either returned or joined us for the first time with one common goal: to share their valuable insights, research, and news with the community. The expo area was swarmed by infosec enthusiasts and partners who exchanged ideas. Many even competed in the 10 hacking challenges designed for the Hacking Village.
Some might have noticed that the DefCamp Capture the Flag area was a bit different this year. And they would be right, because…
D-CTF 2022 went full Attack & Defense, for the first time!
The earliest and most thrilling security CTF competition in Central and Eastern Europe went from a Jeopardy-style online qualification phase to a first-time Attack & Defense-style onsite final, with challenges hosted on CyberEDU. Here’s the D-CTF 2022 walkthrough!
The D-CTF 2022 qualifications were rough
Rough as always, not going to lie. We counted:
- 480 registered teams,
- Over 1,200 participants,
- From 89 countries,
- Who competed for 30 hours for their place in the final,
- Who submitted a total of 2,712 flags,
- And 18,051 wrong attempts.
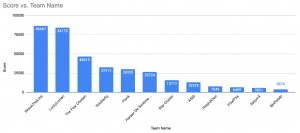
The outcome? See the finalists’ leaderboard for yourself:
| Rank | Team | Country | Points |
| 1 | The Few Chosen | Romania | 6935 |
| 2 | Wreck the Line | Romania | 6435 |
| 3 | Lucky Lucian | Poland | 5992 |
| 4 | SaturnX | Republic of Korea | 5499 |
| 5 | YoloSw4g | France | 5478 |
| 6 | ASIS | Iran | 5056 |
| 7 | ISITDTU | Viet Nam | 4642 |
| 8 | P3WP3W | Romania | 4585 |
| 9 | Hackeri de sentimente | Romania | 4285 |
| 10 | Phish2Own | Germany | 4192 |
| 11 | STT | Portugal | 4171 |
| 12 | BinPotato | Romania | 3835 |
| 13 | panik | Romania | 3371 |
| 14 | StarCluster | Romania | 3171 |
While in the qualification phase, the teams competed against each other but not really directly. However, things were about to change in the final. They packed their snacks, energy (drinks) and knowledge for the first-time ever Attack & Defense D-CTF final in Bucharest, knowing exactly what they were getting themselves into!
What’s different about Attack & Defense?
It’s not just about getting offensive, stealing flags and winning points.
In an Attack & Defense competition, each team receives a set of virtual machines and an infrastructure simulating vulnerable real-life applications and systems. The goal is to fix the vulnerabilities and keep their systems operational, but also attack other teams to gain access to their services and exfiltrate information – all the while being under attack from competing teams and in a race against the clock.
That makes Attack & Defense also about:
- Understanding the attacker’s mindset;
- Identifying quickly the risks and weaknesses in the infrastructure to timely patch threats;
- Developing defensive and monitoring skills, aside from offensive ones;
- Devising the proper strategy that allows you to both defend your services and attack others.
The Attack & Defense experience at D-CTF 2022 looked something like this…

To be more specific:
- 12 teams attended (for the two that couldn’t attend, we’re really looking forward to having you with us next time!)
- They received 30 virtual machines (including the infrastructure),
- 1 hour to get ready,
- And then proceeded to compete in 240 rounds of 120 seconds each – the organizers added vulnerabilities with every round.
The traditional overnight competition model was left behind to make room for a more extreme D-CTF experience compressed in only 8 hours. We didn’t make it easy at all, but we hope we made it fun.
The stats were definitely impressive:
- The highest score was 86,667 points out of 100,000,
- While the lowest was 3,674.
(spoiler alert: unofficial version of the leaderboard incoming!)
- There were a total of 39,271 stolen flags,
- Which means there was an average of 80 stolen per minute.
- The average uptime for functional services was 58%.
And the (official, retro-like) leaderboard was even more impressive:

Get to know the D-CTF 2022 winners better!
1st place
Remember Wreck the Line? They won the last edition of D-CTF as well!
With 22h left on the clock, we became the first team to solve all the challenges at DefCamp CTF #dctf🏆
This concludes our quest to conquer gold.
Cheers to @DefCampRO and @cyberedu_ro ✌️ https://t.co/8BS08ngWOi— WreckTheLine (@WreckTheLine) February 12, 2022
An exceptional performance, as always, achieved by their strong commitment, passion and perseverance. We’ll keep a close eye on what they’ll be up to next time. White hats off!

2nd place
Let’s also give a big round of applause to Lucky Lucian, the team from Poland who came in second! We wouldn’t call them lucky, but hard-working and tenacious newcomers who managed to score so high in the rankings!

3rd place
The Few Chosen is a name to remember, because they are winners of the 3rd place and the best team from Romania as well! Can you believe they are just university students?


Bonus!
Additionally, we’re giving a special shoutout to YoloSw4g, not only for their great scores, but also for sharing their story (and strategy) at D-CTF 2022 on their blog!

And we thank everyone who enjoyed, took pride and spread the word about their D-CTF experience!
It was indeed intense #DCTF but a great experience for my first time @DefCampRO. Attack/Defense is a different beast from other CTFs. See you tomorrow #DefCamp https://t.co/AluxvQOViE
— LazyTitan (@LazyTitan33) November 10, 2022
Of course, our words of gratitude also go to the Orange Business Services and Bit Sentinel teams, for powering the 2022 edition of D-CTF, and to CyberEDU, for hosting us again!
Towards D-CTF 2023
Has this edition of D-CTF swayed us to pursue the path of Attack & Defense for next year’s final as well?
Maybe…
We’re already visualizing modular vulnerability systems, adding more device types…
Until then, stay tuned for Part Two of the DefCamp 2022 Wrap-Up!

