2021 was a challenging year to say the least. The world continued most of its activities fully online which left lots of open doors to cybercriminals around the world. Cyberattacks kept the headlines busy throughout 2021 as massive disruptions affected government agencies, major companies and even supply chains for essential goods like gas and meat.
In these uncertain times, we need to keep the community together, strong and focused to face all threats and keep up with the attackers around the world. We were eager to reconnect with the DefCamp community after a one year break and we hoped to host the conference in a hybrid format.
With all the latest national restrictions, we were forced to move fully online. However, we did our best to offer a valuable and insightful experience with over 40 speakers and over 10 hacking activities that took place on CyberEDU.
How was DefCamp 2021?
DefCamp has been a community event from the very beginning. It started back in 2011 as a meetup between friends that shared a common passion for cybersecurity and in a couple of years became the largest cyber security conference from CEE. Our mission was always to nurture and grow a healthy community of professionals and to encourage young students to join this amazing industry.

DefCamp 2021 was different from any other edition so far. We are strong believers in the power of the community, we always appreciate quality networking and our main goal is to offer our community a legendary experience.
This year, because we had to move fully online, we adjusted the schedule so that we can handle everything the best we can, given the circumstances. And from the feedback received from the participants, we are happy to see that we’ve accomplished this mission.
We are well aware that full online cannot replace the traditional DefCamp or even the hybrid version but we always put safety first. Like we preach in cybersecurity, preventive measures are better than reacting to incidents/issues. So, all in all, we are satisfied with how everything turned out.
Over 40 speakers accepted our invitation or applied at Call for Papers to be part of DefCamp and reconnect with the community. We welcomed both new speakers and traditional ones that come back every year at DefCamp with fresh and exciting research.
To make the experience more engaging, we had 4 panel discussions on different topics as presented below:
| Threats and lessons learned during the pandemic | Ladies in Cyber Security |
| Cybersecurity – the fine line between technology and the human element | Entrepreneurship in cybersecurity – should I go there? |
The topics were diverse as we wanted to learn from each guest speaker’s experience and discover their view on the subject.
You can go through the DefCamp 2021 brochure here.
What was the novelty this year?
2021 has been very intense. As you know us, we always like to bring something new with every DefCamp edition. That’s why we ask for your feedback and we try as much as we can to incorporate it in what we do.
So about the novelties of DefCamp 2021 – well first of all, DefCamp turned a decade in age this year. 11 editions but 10 amazing years where we’ve grown, learned, experienced, cried, laughed and – the most important – we’ve built an amazing community of professionals with the support of our partners who believe in us and help us every year to break the limits and move the extra mile.
Also, what is relevant to mention is the fact that we had 9 new competitions in the DefCamp Hacking Village that demanded the community to put their skills to the test while solving the challenges available directly on the CyberEDU platform.
What topics did the speakers present on stage?
The two virtual stages welcomed over 40 speakers from all around the world. From penetration testing management – problems in large corporations to responding to the ever evolving threat landscape, we learned directly from industry leaders what are the most common challenges and how to better tackle them in our daily activity.
Another interesting presentation was about Training SecOps: Education through Gamification where Ioan Constantin, Cyber Security Expert at Orange tackled some of the biggest hurdles in learning cybersecurity – the “no fun” parts. He shared insights about how they are gamifying cyber-range-as-a-service technologies and how they’re offering a unique and powerful toolset to companies and academia to train, assess and enable continuous learning in cybersecurity for their staff and students. Ioan highlighted how education through gamification can pave the way for next-generation Security Operations Centers and we’ll see how all of this translates to performance in UNbreakable Romania, a first-of-its-kind National ongoing Cyber Security Competition.
Moving forward we’ve tackled automotive security. Because vehicles are getting increasingly complex, connected, and automated. The dynamic digitalization and an evolving regulatory environment bring higher automotive cybersecurity requirements. Jan Glos, Algorithm Development Engineer Garrett – Advancing Motion, focused his presentation on the cybersecurity needs passenger and commercial vehicle makers have, how those requirements are fulfilled, and how the dedicated tools are developed and tuned.
And because there isn’t a day without any cyber attack or incident, we enjoyed the presentation that Danny Henderson Jr., Senior Information Security Advisor Secureworks named “Curse of the Mirage Forest: An Incident Responder’s Tale”. Because threat actors continually improve on their ingenuity on staging ambushes, like bandits within a dense forest. Whereas the typical entry of breaches start with phishing, the more clever tricksters cloak their trap through a Mirage spell within a simple clearing, enticing unsuspecting business that failed their Insight check to claim a trojanized program. The tale included a close-call encounter with the adversary in an incident response call, how they tracked the bandit’s trail, and shared the ways that other adventurers can follow-suit in using available free services for threat intelligence to aid crafting their own tales.
Moreover, we’ve seen how much ground ransomware attacks gained in the past years so it was an absolute pleasure to have on the virtual stage Radu-Emanuel Chiscariu, Senior Security Research Engineer Keysight Technologies sharing A Deep-Learning Approach to Phishing Detection. A common tactic for adversaries to harvest credentials and personal information is through phishing websites. To increase the probability of a successful attack, the attackers try to closely mirror the look of a legitimate website, hoping to trick their target. There are various approaches to detecting phishing pages that focus on extracting source code features of the website. Radu focused his presentation on creating an overview of how such an approach would be implemented using a deep neural network and its accuracy in identifying phishing pages.
We’ve seen that many companies and publications talk about threats but what about how to detect them in order to be protected before they target your company? Well, we had on the DefCamp 2021 virtual stage Raphaël Lheureux, CSIRT & Pentesting Team Leader CEGEKA who explained how to leverage threat intelligence in the selection and prioritization of detection sources. Raphael shared his take on how cybersecurity professionals usually know which detection sources are required to cover most of the threats that an organization could face. In reality, there are several reasons why not all of these can be onboarded within a reasonable timeframe, or even at all: limited budget, slow and/or complex change management, concerns around manageability etc. So he focused his talk on presenting an approach to address this challenge using MITRE ATT&CK and other threat intelligence sources.
Surely the time would never be enough to tackle all the subjects we would like to have on stage at DefCamp but we believe the diversity of speakers and topics managed to cover important aspects from the infosec industry.
What about the Hacking Village?
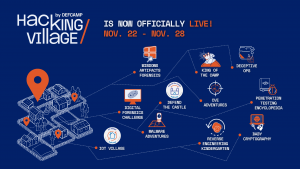 Well, you know how it works. The Hacking Village has been the DefCamp playground for all hacking activities since 2016. Since then, we hosted more than 50 cybersecurity competitions to keep the community engaged.
Well, you know how it works. The Hacking Village has been the DefCamp playground for all hacking activities since 2016. Since then, we hosted more than 50 cybersecurity competitions to keep the community engaged.
2021 was the year of change so for the DefCamp Hacking Village this meant new & different competitions along with the traditional ones to keep the community engaged. You can see here an overview of what the Hacking Village had to offer this year.
What is important to mention is the fact that the competitions available were very diverse and covered many cybersecurity skills: from penetration testing to digital forensics, reverse engineering and cryptography. For one week, all DefCamp attendees could have enrolled in the contests and tested their skills in the most active part of DefCamp.
The most popular one was CVE Adventures where attendees were challenged to test their vulnerability scanning skills, exploitation skills and ability to find exploits published by the security research community, all in a safe environment.
IoT Village was also on the favorite list as it was the only hybrid competition available this year. With the support of Siemens we managed to bring closer to the DefCamp community the IoT devices hacking.
What’s next?
Our plans for 2021 definitely looked different. But this year’s DefCamp edition will forever remain special to us in its own way – and we hope you feel the same. It’s been great to have your virtual avatars around and we promise to do everything we can so we can see each other face to face, like good old times, soon.
We look forward to 2022 with the same passion for cybersecurity, with the ambition to grow and nurture cybersecurity skills and a strong community ready to keep up with the attackers around the world.
Until 2022, stay safe, hacker family!

