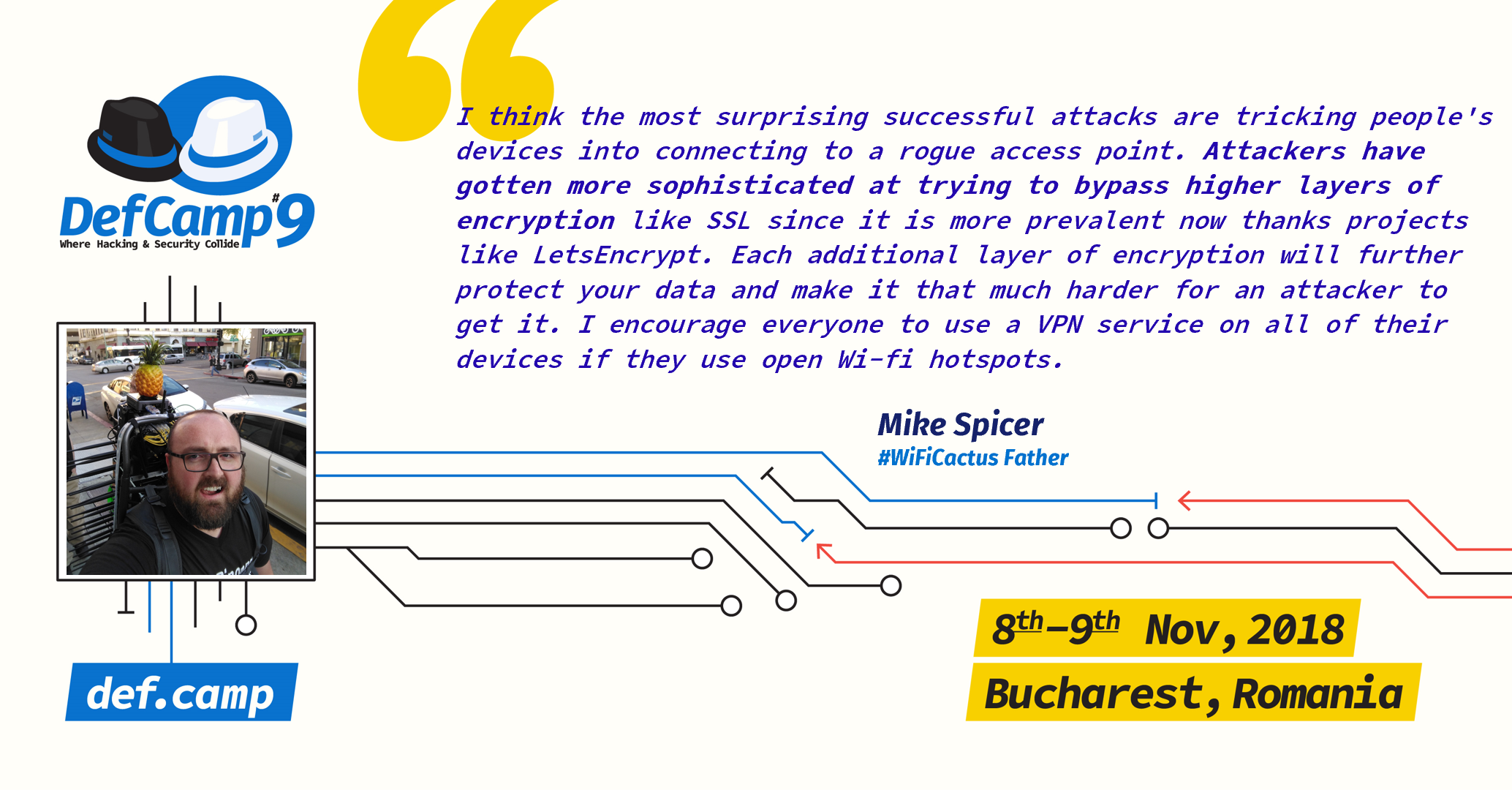
Mike Spicer was on stage at DefCamp 2017 for the first time and those who attended the conference probably remember him as “the guy with the giant backpack” and the pineapple.
All the while he was there, he wore a big (and frankly intimidating) device called the “Wifi Cactus”, which is a wireless monitoring tool that is capable of listening passively on 50+ channels of WiFi at the same time.
The good news is that Mike Spicer is coming again to DefCamp #9 this November and he will share news and updates about his awesome project.
Last year, Mike was a sensation and all the DefCamp attendees were captivated by the device and how passionately he spoke about it.
That’s why we were curious to find out how he’s planning to keep the audience engaged and spice up the presentation again this year.
He shared with us that traveling to Romania for DefCamp with the #WiFiCactus was an amazing experience. He learned a lot about what he needed to improve on the project to make it more effective.
Over the last year, Mike has made significant improvements that have increased the amount of data the Wifi Cactus is able to capture. He also improved its mobility by reducing the weight, and he added Lithium batteries to increase run time. Additionally, he improved his data analysis techniques and he’s excited to share more details at the event.
“I believe talking about the improvement process and lessons learned will be engaging for the audience”, said Mike.
Knowing about its obsession with wireless and all the knowledge he has about this subject, we asked him to share three key wireless monitoring pitfalls companies should avoid at all costs.
His answers are insightful and packed with actionable and very useful examples:
1. “The first pitfall I think should be avoided is trusting a vendor to perform monitoring for you. With the availability of open source software like Kismet and extensive driver support, anyone can begin performing wireless monitoring and know what is in the airwaves around them. Adding in-house monitoring to your SOC will empower your team to have better defenses.”
2. Another pitfall when performing wireless monitoring is trying to do it all by hand in something like Wireshark. The amount of data collected can be daunting and analysis on large amounts of data will be slow. Instead, Kismet, for example, does filtering and detection of common wireless threats. Other software has these capabilities too and should be explored if they are already deployed in your environment.
3. The final pitfall that should be avoided is not having a strategy for how and what you want to monitor. Additionally, Mike insists “you need to think about how large your organization is, and the reach of your wireless network.”
He recommends companies to “build a coverage map as a baseline, identify and think about their weak security spots and then perform monitoring within an organization to see if anyone is attacking it at those locations.”
Here’s an example: “Your wireless coverage could be bleeding over into a neighboring parking lot. Potentially you could see injection attacks coming from an unknown device toward one of your access points or clients and now have a log of that behavior that can be reported to authorities or handled internally.”
Wi-fi attacks still represent a serious, sometimes inconspicuous security threat. The danger lies in the pervasiveness of hotspots and the multitude of ways in which malicious actors can compromise them.
We wanted to know Mike’s opinion on how cybercriminals use the surprise factor during these attacks and how people can protect their sensitive data from eavesdroppers.
“I think the most surprising successful attacks are tricking people’s devices into connecting to a rogue access point. Attackers have gotten more sophisticated at trying to bypass higher layers of encryption like SSL since it is more prevalent now thanks projects like LetsEncrypt. Each additional layer of encryption will further protect your data and make it that much harder for an attacker to get it. I encourage everyone to use a VPN service on all of their devices if they use open Wi-fi hotspots.”
Since the Wi-fi technology is widely used these days, it brought us to another key topic:
How Wi-fi technology might evolve over the next few years and what security standards will make public Wi-fi safer for users.
Mike mentioned that “open wireless networks are a necessity to many people” and shared his excitement about WPA3, the next generation of Wi-fi, which will have a solution called Enhanced Open, and offer strengthened security and better features for Wi-fi devices.
Finally, we asked Mike to share some essential career tips for enthusiastic teenagers who are trying to figure out if cybersecurity is the right career path to follow:
- “I would recommend that they first start with learning networking. How devices communicate is fundamental to understanding how to secure them.
- Next, I would tell them to learn a programming language like Python and use it to explore how network applications work.
- Finally, I’d recommend that they build a project that answers questions they have about a certain part of security. For example, I was curious about how dangerous the wireless network was at DEFCON in Las Vegas which led me to build a wireless sensor that fits in my backpack. Eventually, that project turned into the #WiFiCactus.”
We kindly want to thank Mike for taking the time to provide these insightful answers for our interview and wrap up with a key piece of advice he said:
“I think it is extremely important to be constantly curious and to explore the limits of what is possible to thrive in cybersecurity.”
Make sure you don’t miss Mike’s talk on Year of the #WifiCactus at DefCamp #9 this November!
The interview & editing was made by Ioana Daniela Rijnetu
DefCamp is powered by Orange Romania and it’s organized by the Association “Research Center for Information Security in Romania” (CCSIR).
DefCamp 2018 is sponsored by Ixia, Keysight Business, SecureWorks and Intralinks as Platinum Partners and it’s supported by IPSX, Bit Sentinel, TAD Group, Enevo, Crowdstrike, CryptoCoin.pro, Siemens, Alef, UiPath and Kaspersky Lab.