Data Protection is nowadays a hot topic to any industry, whether we are talking about private companies or governmental institutions. This is why, we’ve proposed Yury Chemerkin, speaker at DefCamp in 2015 and 2014 to tell us a bit more about how companies and individuals are working on this threat.
Data Protection is nowadays a hot topic to any industry, whether we are talking about private companies or governmental institutions. This is why, we’ve proposed Yury Chemerkin, speaker at DefCamp in 2015 and 2014 to tell us a bit more about how companies and individuals are working on this threat.
Yury, you are multi-skilled security expert, what is your key field you are working in?
I have an experience in reverse engineering, secure development and familiar with AV industry. I’m mainly focused on privacy and leakage showdown. It involves different activities of exploitation based on misunderstood security principles and developing. Many times it’s driving to the simplest ways to perform attacks to get access to the data in mobile field or somewhere else.
I heard about lot of mobile vulnerabilities happened last time. For example, FireEye wrote about iOS Masque Attack
Yes, it was a well-known way to bypass iOS security controls. Similar technique was possible for Android OS too but fixed a bit earlier. There were several reports and conference talks a long time before FireEye confirmed it as a spy approach in 2015. It made vendors to fix it quickly. You know, it’s really hard to believe the security team missed several researches how to inject malicious payload into real applications to transform these applications into fake copies. It really simplifies getting an access to the data without breaking the security controls implemented in mobile applications.
However, all these attacks require a solid experience. You mentioned simple attacks happen sometimes.
Exactly, when we are talking about difficulty of attacks, you should keep in mind that security and anti-security field have grown much and have been under the fire last several years. Many applications had various issues on data protection. Many applications are seemed built in a manner one-time application but suddenly grew up into big startup.
Could you tell a bit more about it?
Sure! Not spreading gossips on whom or what makes us insecure, the most popular answer is any ‘customers’. I bet you heard about it many times from news or your security team directly. However, we have three underlying problems because of conflict of interests.
First of all, people share information about themselves and you can read about it. For example, it is old story but it happened once again recently. Security research investigated how much data can be extracted from fly ticket barcode. Frankly talking, all information published on the fly ticket in plaintext equals to the data stored in the barcode. He said this is enough to get access to your loyalty travel account and know about your travel details and loyalty membership. You can get more details from this link.
Second problem is a lack of knowledge about security. It is difficult to fix because you need to train people and no one wants do it for free for a long time and because developers don’t even try to make their applications a bit secure.
Here is third problem – developers are not going to be responsible for their fail. They can continue talk to you that is everything works as intended, they can fail with implementing security controls, and they can make different mistakes to ruin the security. But one big problem is humans fail and developers are humans too, they have to admit it, unfortunately. I give you example, I was going to check how my customer data protected. If developers don’t tell me that, I have a right to know it. I registered myself on the Hotels.ru web-site and get an email in return. This email had a piece of information that includes my account credentials in plaintext. Yes, including my password! I was staring at this email. I bet you don’t know what next line was. These guys were telling me in this email “We guarantee the confidentiality of your data.” I didn’t examine their mobile application on data protection even, they already fail with it. In addition, this application transmit all information via http in a plaintext.
That was unexpected. So, are you relying on how data protected in your researches without taking vulnerabilities into account?
We need to define several levels of data protection. Your data can be stored or transmitted over the network in several forms: without any kind of protection (plaintext), weak protected (nothing special to decrypt the data), medium protected (need to make do something), protected (attacks prevent but we can’t be sure that everything is OK) or h4 protected (when we examine current build of application and confirm the security until the device is jailbroken or rooted). Also, the security controls are system or own developed. From this point of view almost of all these attacks are pretty easier without vulnerabilities. Your security may cost $500 and it means, $500 spent on buying licensed software to perform attacks, however you can get a free pirate copy as well. Pro software costs more $1,5k but vulnerabilities cost more.
Ok, if I’m using the public network I believe the paid network is better than free network, right?
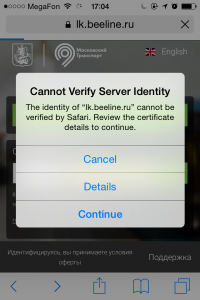
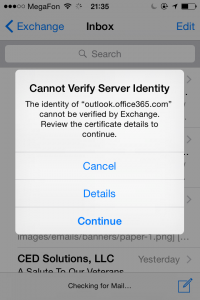
Paid network helps to encrypt data because paid networks usually make users to type credentials they received due to registration. However, I was in situations when I couldn’t say which one is better. This year I arrived in Bucharest Airport and my device discovered a public free network in the airport. After connecting, I open several applications that prevent MITM attacks in certain ways. For example, British Airways app prevents MITM attacks if you’re in untrusted network and someone is trying to steal your data. App prevents you from accessing the server if you’re looking for flights or buying tickets. Meanwhile, other applications worked very well in the same network. Another time I was in JFK airport in New York, USA. I was using prepaid network Boingo WiFi and got a warning message about untrusted certificate from Microsoft server when I was checking my email. Moreover, I had several device and all native BlackBerry apps stopped working in that network. Only 3rd party apps continued working. Same happens to me in Russian public WiFi network in underground rapid transit (Vmet.ro). Talking about it, we had a PHdays and Zeronight conferences where one speaker recreated a fake WiFi network parameters of VMetro that, in turn, made guest devices be connected to this fake WiFi network.
Check two screenshot, first one was made in JFK airport, second is in Russian public WiFi network in underground rapid transit.
So, I have still to know about each application how it’s secure, right?
Yes, you have to be informed about each data type (credentials, mails, etc.) per each application you use and per each OS because there are some difference in how app was developed for different OS.
Frankly talking, your Android app maybe does more security in preventing attacks than iOS app.
What are your thoughts about insecurity, what the cornerstone problem is?
We have many issues here beside the user actions that lead to data leakage. Developers usually don’t spend enough time to protect customer data. But another problem is growing quantity of startups and outsourcing developer teams. Startup teams obviously don’t have a time to protect data; outsourcing teams don’t receive requests to protect data from the business teams. Also, there are many 3rd party services that help to build you network, backed or mobile application even in 5-15 minutes. They also may not provide a security at all. I give one more example, Kinvey is good 3rd party service to store data and provide you with user role management. You can let users register themselves via app that makes requests to the Kinvey in turn. After that, you got a personalized account and can put customer data into appropriate folder protected from others. But, Kinvey isn’t able to protect network data from MITM attacks. I built a test application and was successful in intercepting credentials and URLs to download data.
What companies do usually tell when they have known about insecurity?
There are many researcher who did same researches. So, I just refer to public answers available on Internet. According to this link, Instagram said they were moving to encrypted communications for its images by moving to HTTPS, the secure version of the standard used to transfer Web data over the Internet. Before 2014 they sent media data in plaintext without any kind of protection. Now, they did it moved to https but it’s still affected to MITM attacks.
4talk team wrote in GooglePlay description the statement “SECURITY is core at 4Talk. Starting from secure phone number registration, to interaction only with confirmed personal contacts, to fully managing your account from any device you use.” Facts are in 2014 app wasn’t protected at all, in 2015 Windows Desktop app is protected for in-rest & transit data and prevents MITM,
Android has a protection of network layer only, but iOS and Mac OS apps don’t have any protection at all
.
And the best quote from AgileBits team who insisted that AgileKeychain was still secure, and noted that the format dates back to 2008 when the company was concerned about speed and battery drain problems caused by encryption. Saying honestly, there was no problem in 2008 even with battery draining. Let’s assume this problem still exist. AgileBits develop 1Password application to keep your data like credentials secure. Size of database if you’re active user even is not really big; this app doesn’t transfer or encrypt gigabits of information. Instead it’s really small, several MB. Moreover, if you’re security developer, you have to be responsible for giving enough security and fixing issues at the time.
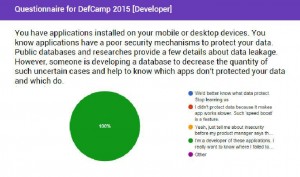
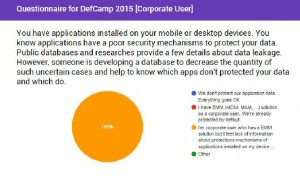
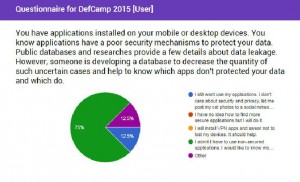
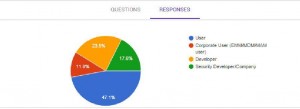
Are there any researches or public polls that confirm user’s interest in implementing protection techniques to keep their data secure?
It’s hard to find but still there are. One of them is a research made by ITR and available here. According to their research, there’re 30% ‘angry men’ who want uninstall your app because privacy concerns. Isn’t it funny to continue telling us vulnerabilities make sense and data leakage doesn’t.
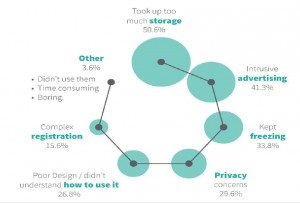
Also, my poll was published prior to DefCamp conference confirmed same results.