When you’re fully emerged in infosec, always focused on solving problems that emerge and multiply endlessly, you sometimes forget to celebrate the wins.
Here’s a small, but important one to think of: encryption is now on almost everyone’s lips (or at least in some corner of their minds). What used to be an exotic concept in which only a select few dabbled, now people from all over the world have it as a default in some of their most important apps.
It may feel like the challenge to make encryption a standard throughout the tech world has just begun, but we’ve progressed quite a bit!
Given how important this topic is for the infosec community, we couldn’t have missed adding it to our agenda. In a few weeks, you’ll see Cosmin Radu live on the DefCamp stage, showing how to about “Burp-ing through your cryptography shield”.
Cosmin is an Information Security Consultant within the Penetration Testing Team at Atos, in Romania, but his interests and expertize don’t stop there. He’s also passionate about Web Applications, Operating System Security and Network Security, and never misses a chance to learn something new.
Neither do we, so we just had to pick Cosmin’s brain and find out more about the prevalence of cryptography attacks. Lucky us, we got more than we hoped for, including varied examples of such attacks.
First and foremost I would like to say that even though it seems like cryptography attacks aren’t targeting you or that you are not affected by them, they are out there, and they can and will affect you.
In the past couple of months or years, more and more cryptography flaws have emerged in everyday software which is used all over the internet. Even more, they can affect your home router, the gatekeeper to all your online actions and secrets. I could mention attacks on WPA2 – KRACK or attacks which target the secure communication between your browser and the servers in the cloud(i.e. RC4 stream cypher), or even in Crypto Coin wallet implementations. And those are just a few examples of attacks which have sent a shiver down the spine of many users around the world.
Certain problems can appear with cryptography when you “write your own crypto”. I am not a cryptographer, but if there is one lesson that I have learned is that you should Never Write Your Own Crypto. The algorithms out there are tried and extensively tested and should be used. I personally have seen vulnerable crypto implementations in apps out in the wild.
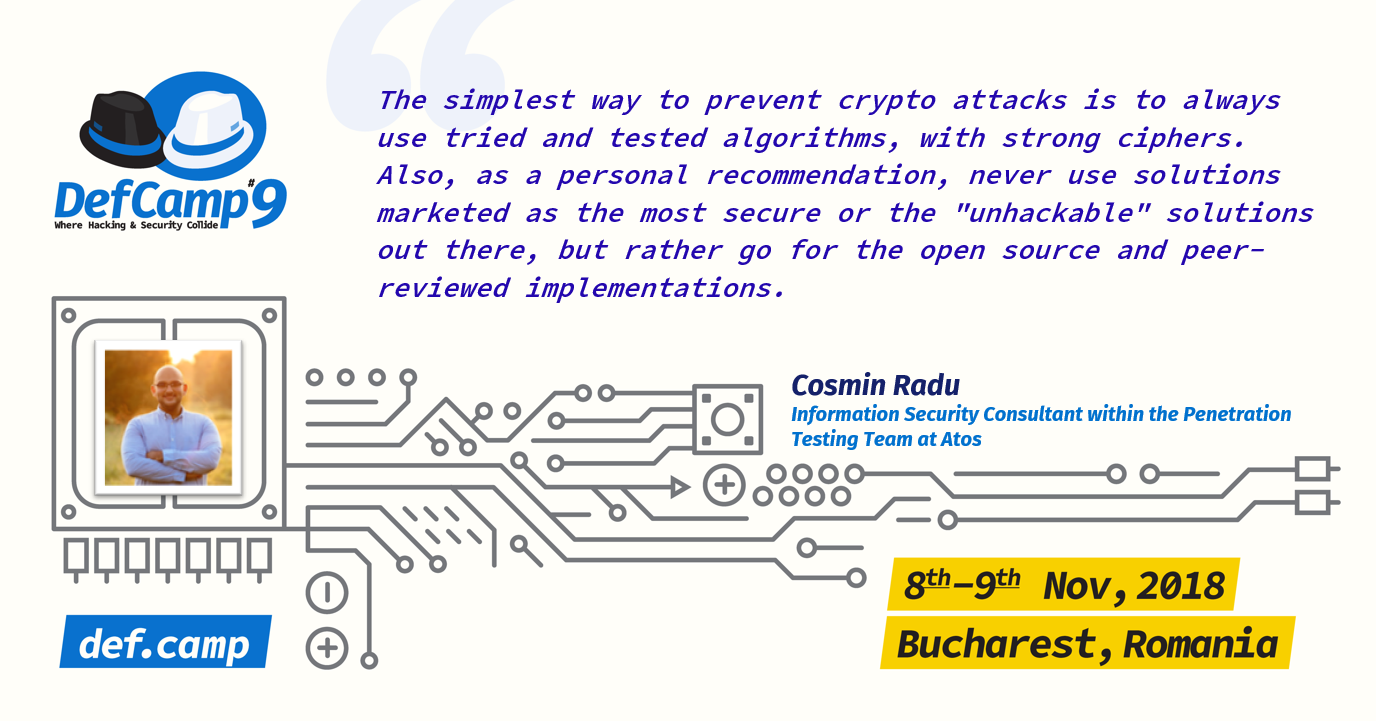
The simplest way to prevent crypto attacks is to always use tried and tested algorithms, with strong ciphers. Also, as a personal recommendation, never use solutions marketed as the most secure or the “unhackable” solutions out there (n.a. read about the Bitfi wallet), but rather go for the open source and peer-reviewed implementations.
Cryptography flaws create opportunities for malicious actors to target a large number of victims but attacks using encryption are significantly more frequent.
The classic use case still remains in bypassing security solutions by encrypting communication to Command&Control servers, and maybe also the message itself in a double encryption approach.
Another big trend is abusing the release of Let’s Encrypt and the simple way it offers to provide the „green lock of security” in browsers, which increases the risk of users trusting phishing websites.
Clearly, there’s a lot of different challenges to tackle as a cyber security specialist focusing on cryptography. That’s why we couldn’t miss the opportunity to ask Cosmin what he recommends an aspiring ethical hacker do to start building her/his experience in the field.
Disclaimer: the stages may not as easy as Cosmin describes them, that is, until you’ve gathered some practice under your belt.
The first steps that I have taken include reading about cryptography, maybe start from a plain resource like Wikipedia, read the material that is referenced in the wiki page, build up your vocabulary.
Follow an OpenCourseWare online on the topic, something on the lines of Cryptography 101.
The next step might be to use a tool like CryptTool and visualize how the algorithm works.
Following that would be to implement one or more of the algorithms out there using libraries such as OpenSSL or BouncyCastle.
After that, start researching algorithms that are vulnerable, understand why they are vulnerable, exploit them.
Let’s not forget that, while experts are engaged in their meticulous practice, the connected world is starting to expect encryption as part of the basics more and more frequently. (Security and privacy advocates, your voice is being heard!)
However, that doesn’t mean it makes it easier to understand. Here’s what Cosmin believes it will take for encryption to become common knowledge:
In this era of communication, of third parties everywhere having access to your data for the right price, of governments spying on everyone, encryption brings an ease on one’s mind. It allows you to relax a little while surfing the Internet.
This perception will change by „force” because nowadays heavy internet corporations are investing in widespread encryption as a default for users. Just take a look at Google and Chrome and their approach to mark unsecured websites, and Facebook with encrypting communication for the users of Facebook Messenger and WhatsApp.
The more privacy and security end users demand from software and hardware makers, the more these makers are going to focus on building them. It won’t be a perfect process, but it will still mean progress.
Cosmin believes:
It is important to address the security concerns and solutions for the end users.
A part of the overall security of an environment is also influenced by its users, and thus raising awareness on the potential vulnerabilities that they are exposed too by not using proper security baselines should be in everyone’s attention.
Encryption should be a term that everyone can relate to, focusing on both privacy and security. I think the media should promote to non-technical users more about what is, and why encryption is useful.
If you have as many new questions for Cosmin after reading this interview as we have, join us at DefCamp #9 on November 8-9!
We’re a few short weeks away and can’t wait to learn more from Cosmin about experimenting with cryptography and its infosec applications!
This interview was made by Andra Zaharia. You can get in touch with her on LinkedIn or say hi on Twitter.
DefCamp is powered by Orange Romania and it’s organized by the Association “Research Center for Information Security in Romania” (CCSIR).
DefCamp 2018 is sponsored by Ixia, Keysight Business, SecureWorks and Intralinks as Platinum Partners and it’s supported by IPSX, Bit Sentinel, TAD Group, Enevo, Crowdstrike, CryptoCoin.pro, Siemens, Alef, UiPath, Atos and Kaspersky Lab.